Hacking electricity, water, and food
As we keep saying, it’s very important to be aware of the latest cybersecurity news and threats. Being prepared is more than half the battle.
However, even those who know everything there is to know about cybersecurity, who use reliable passwords and regularly change them, who recognize phishing messages at a glance and protect their devices with a top-notch security solution — even those who do everything right — are not completely safe. Because we all live in civilization.
The thing is, we have control over our personal devices, but industrial equipment is far beyond our reach.
Cybersecurity? But we bake cookies!
Our cybersecurity experts undertook a study to find out where things stand with industrial control systems safety.
Shodan, the search engine for connected devices, showed us 188,019 industrial systems in 170 countries that can be accessed on the Internet. The majority of them are located in the United States (30.5%) and Europe — mainly Germany (13.9%), Spain (5.9%), and France (5.6%).
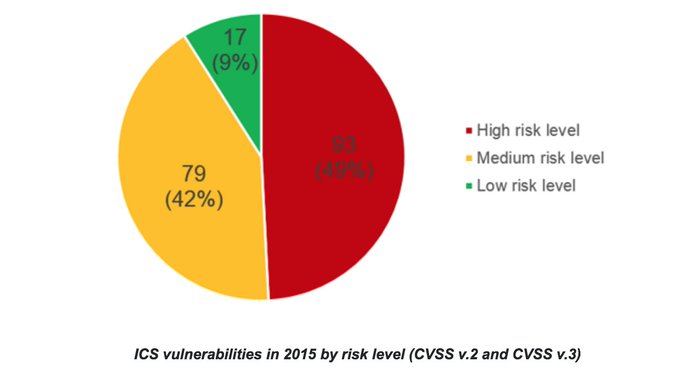
A whopping 92% (172,982) of the industrial control systems (ICS) detected are vulnerable. Shockingly, 87% have medium-risk-level bugs and 7% have critical issues.
In the past five years, experts have thoroughly examined such systems and found a lot of security holes: During this time period the number of vulnerabilities in ICS components increased tenfold.

Of the systems our experts analyzed, 91.6% used insecure protocols, giving criminals the opportunity to intercept and modify data using man-in-the-middle attacks.
As well, 7.2% (about 13,700) of the systems belong to huge companies in aerospace, transportation and power, oil and gas, metallurgy, drinks and food manufacturing, construction, and other critical areas.
In other words, skilled cybercriminals can influence any economic sector. Their victims — hacked companies — will hurt thousands or millions of people by supplying them with tainted water or inedible food, or by turning off the heat in winter.
What does it mean for all of us?
The possible effects and outcomes depend on which companies cybercriminals target — and what ICS those companies use.
We have already seen the results of some industrial hacks. In December 2015, half of the houses in Ukrainian city Ivano-Frankivsk were under blackout because of an APT Black Energy attack. The same year, an attack at Kemuri Water Company was discovered as well. Cybercriminals had penetrated its network and manipulated the systems responsible for adding chemicals to clean the water.
In addition, Warsaw’s Chopin Airport was also attacked by hackers. Moreover, a year earlier, criminals disrupted the operation of a blast furnace on a steel mill in Germany.
Black Hat and DEF CON: Hacking a chemical plant
Since there’s nothing unhackable in this world, why should chemical plants should be the exception?
Overall, the security of industrial control systems leaves much to be desired. Kaspersky Lab has repeatedly issued warnings about these risks, but naysayers usually parried: Tell us about realcases where these vulnerabilities were actually exploited. Unfortunately, we can now do that.
Of course, one person alone can do little to solve a systemic problem: Industrial equipment cannot be changed in a day or even a year. However, as we’ve already said, the most crucial cybersecurity defense is knowledge. The more people aware of this problem, the greater the chance that critical industrial infrastructure will be patched before anything really, really bad happens.